We offer our email service users generous disk space allowance and the ability to use an address with their own domain. However, most other providers also offer these features. Providing a good email service is hard work. There are several other key areas we excel at, which makes our email service stable and dependable. Read on to see what we do to have such a happy customer base.
How Email Service Works
When people think of email service, they usually think of the service as a single thing. However, in reality, the email service consists of many software products that work together to create a smooth experience for the email user. For example, when a message is sent by one person to another, the message is usually processed by at least four software products before the recipient can read it. And this does not include the email clients of both users!
When a message is sent, the email client of the sender connects to the SMTP software of the sending email service provider. The SMTP software then internally handles the message over to the MTA (Mail Transfer Agent) software on the server. The MTA software then looks up the proper DNS records of the recipient domain, and transmits the message to the recipient server. This happens by connecting to the SMTP software on the recipient server. The SMTP software that just received the message in turn hands it to the MDA (Mail Delivery Agent) software, which saves the message in the proper mailbox on the recipient server. Once the message is saved, the recipient must connect to their mailbox with their email client in order to read it. This usually happens over a POP3 or an IMAP connection, which is handled by yet another software product.
What is SMTP?
SMTP stands for Simple Mail Transfer Protocol, and is the backbone of email communication. Defined in 1982, SMTP is still used by all email service providers today to transmit email messages between servers. Although some email service providers might transmit messages internally via non-standard protocols, SMTP is used to transmit messages to other email service providers.
Server Stability
No one is going to get their emails if the server of their provider isn't fully operational. You already know that sending a single message involves the coordinated work of multiple software products. If any one of these systems is not performing properly, the entire email service might appear down for the user. This is why we take extra steps to make sure all systems running on our servers are always operational.
Even perfectly configured servers need software updates and upgrades from time to time. These procedures often require server reboots, and even hardware module replacements. To ensure minimal impact by such events, we perform planned maintenances only during the small hours of the night. This way, businesses can operate uninterrupted during business hours, and enjoy a reliable email service they can depend on. We also have a team of highly trained professionals that monitor all our servers 24/7. And we don't mean that someone, somewhere will get a pager message if a server doesn't ping back. We mean that a real person is there to make sure every single system on the server is operational. In addition, our custom server monitoring software monitors every single subsystem on our servers to back our team.
Server Security and Reputation
It is definitely not pleasant to send an email, only to find out the recipient server rejected your message. The technology community designed the global email system a long time ago when abusers were not on the radar. This is why email service providers came up with a reputation system at a later date. They did this in order to protect their users from spammers and scammers. Unfortunately, there is no centralized server reputation system. Each email service provider uses their own rules and tests to check server reputation against different block lists. Keeping good server reputation is our top priority. This is why we are constantly performing deliverability tests against some of the most popular email service providers.
The most common cause for poor server reputation is the detection of SPAM messages originating from the server. To prevent this from happening, we have strict security practices in place. First, we make sure all mailboxes on our servers use strong passwords. In addition, we have a dictionary with known compromised password hashes. We use it to prevent users from setting a password that hackers already have. Second, the software on our servers recognizes brute-force attacks, and stops them by denying access to suspicious IP addresses. Third, our team is monitoring the mail queues on our servers for suspicious activity 24/7. Finally, we digitally sign all legitimate messages that our servers send. We also automatically add SPF records for our clients.
Even strictest security practices cannot prevent hackers from using passwords they have stolen elsewhere. When this happens, a quick reaction is vital. This is why we subscribe to the Feedback loop (FBL) systems of popular email service providers. These systems alert us immediately if spam originates from one of our servers. Our team then immediately takes action to close down the compromised account.
Email Filters
It is irritating when you have to go through hundreds of spam messages in your Inbox. To avoid this, we have a sophisticated spam filtering system in place. This system protects the users of our email service from spam messages. Our filter performs most checks and tests on SMTP level. There, our servers check the reputation of the server trying to deliver a message against many block lists. We use only premium subscriptions to reputable block list services. This ensures that the information listed there is always accurate and up to date. Custom rules are also backing up the SMTP level checks. These rules are a direct result of the combined experience of our team.
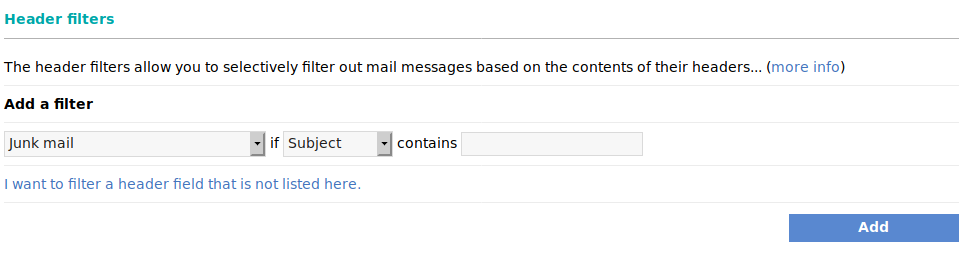
Sometimes, predefined rules are not sufficient for some users who need specific rules in place to block specific messages. This is where the ability of our users to set up custom email filters comes in.
You can easily tune the aggressiveness of our spam filtering system. This is a great asset because it gives the users of our mail service the ability to fine-tune their experience. Moving a simple slider to the left will result in more aggressive filtering. On the other hand, moving it to the right will result in more relaxed filtering. You can do this globally for a domain, or on a per-mailbox basis. Some email providers like Gmail pride themselves on a highly effective spam filter. However, users have no means to adjust the filter to their needs. This makes Gmail's filter overly aggressive in some cases. For example, a Gmail user recently switched their personal emails to a mailbox on our server. He simply could not get the emails from his security camera out of the SPAM folder at Gmail.
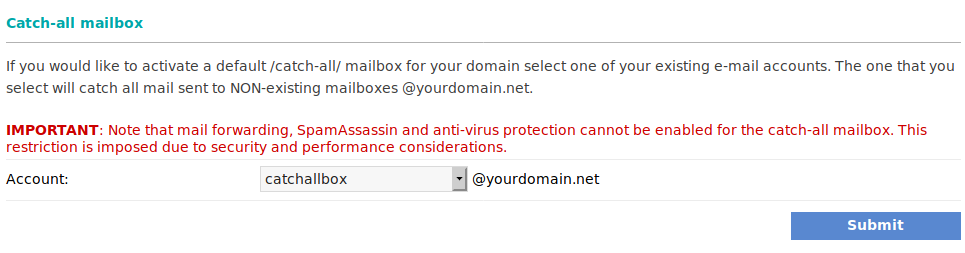
Catch-all Mailboxes
The catch-all functionally we offer is also very useful. This functionality allows you to direct emails sent to non-existent addresses to a particular mailbox. Recently, Apple announced the "Sign in with Apple" feature. They advertised it as a big leap towards enforcing privacy and security. While we don't offer a sign-in service, similar setup was always easily achievable by utilizing a catch-all mailbox. You can sign in to different services with unique bogus email addresses at your domain name. For example, [email protected], or [email protected]. The catch-all functionality allows you to receive the emails sent by these services. Sometimes, service providers sell your data, hackers compromise a service, or you don't want to receive emails from a service. If this happens, you can simply blacklist the bogus email address you use with the service.
Customer Support
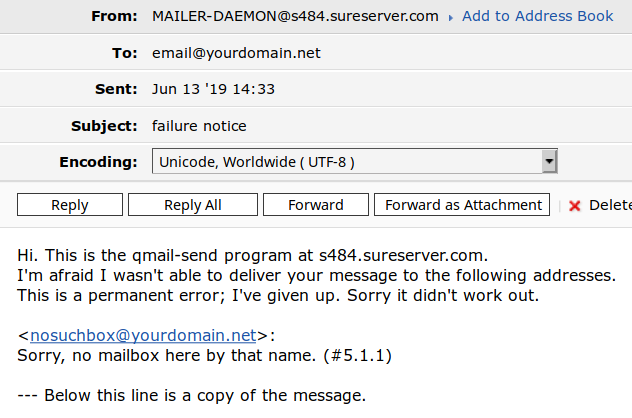
Every once in a while a message will go missing, or you will receive a cryptic error. The only thing left to do is to contact your email service provider and ask them about the missing message. Some providers might take days to give you an answer. With our support team, you will have your response in minutes. Our team will decode the cryptic bounce message you received. They can also investigate the headers of a message, or check the logs on the server for you. Don't believe us? Just give ICDSoft a try.